How do you avoid phishing scams when working from home?
Just like your home, your computer systems will have several layers of protection to prevent the bad guys gaining entry. It’s very difficult to get around firewalls and Virtual Private Networks, just like it’s hard to get through locked windows, doors, and security chains. So, in the same way a burglar may seek to gain entry to your home by posing as a meter reader, a cyber-criminal will use “phishing” scams to get you to willingly invite them into your computer systems. As more and more people are working from home for some or part of the time, they add an extra complication to cyber security that businesses need to be aware of and address.
What is a phishing scam?
At a high level a phishing scam will trick people into doing something that they really don’t want to be doing. Like its name sake phishing uses bait to lure the unsuspecting, often tempting people with goodies like special offers or free cash, or generating a sense of urgency and panic to make people make decisions in a hurry without thinking through the consequences.
Like any good con trick (which is exactly what it is) phishing seeks to gain your trust and uses misdirection to make you to act in a pre-planned way and get you to part with your money or secrets like your usernames and passwords.
The most common phishing attempts are email based with the perpetrators casting out thousands of emails in the expectation that someone will take the bait. The emails frequently work in one of two ways. The emails may contain an attachment which will release malware upon opening to infect your computer. Alternatively, there may be taking you to a fake website. The website will either download malware to your computer, or it may be set up to look exactly like your bank website and trick you into entering your banking username and passwords.
Sometimes the email will be a combination of the two, tricking you into opening an attachment, which may be an innocent looking .pdf file that can sneak past spam filters, but in the .pdf is a link to a dodgy website.
Variations of phishing methods
Spear Phishing
Spear Phishing is a very targeted attack at a single individual or a small group of people. They require a much larger investment in effort from the hacker, but are often more successful and reap a potentially higher reward. Hackers will find out as much information as they can on an individual, using LinkedIn or other social media, sometimes conning staff, suppliers or contractors close to the individual to make it much more likely the target will fall for the trick. An example I read noted a company director had liked a particular florist on Facebook, so the hacker spoofed a “thank you for your order” email from the florist with a money off voucher. Clearly trusting the florist he’d just used the director clicked on the voucher links in the email and set off the malware infection. You can guess the rest.
Whaling
A form of spear phishing that targets top ranking individuals in an organisation. These attacks are often very professional and highly coordinated, but can reap massive rewards.
Clone Phishing
Clone Phishing uses fake URLs that look very similar to real ones. Often swapping the letter “i” for a lower case “L” or an O for a zero. Anyone slightly suspicious of a link in an email may hover the cursor over the link and see that the link appears genuine, even though it isn’t.
Typo Squatting
Preying upon all our abilities to mistype things attackers create domains and websites that are very close to real names and that may commonly be typed accidentally. Hoogle.co.uk or foogle or voogle for example, or gail.com instead of gmail.com.
Other common variations include email account takeover where a hacker learns your email address and password, logs into your email account and sets a rule to forward all incoming emails to their email address and move the message to a sub folder in your account. They can then carry on a conversation posing as you and tricking your contacts into sending them money. I witnessed a version of this sent to someone in an accounting firm, they told the customer to send money to a certain HMRC account, which failed, so they tricked them into sending it to their account so they could transfer it for them before the 31st January deadline, so preying into the clients fears of getting a massive fine for missing the deadline.
You may wonder how an attacker learns your email password. The most common method works because people use the same password for multiple web sites. We’ve all done it. Then when a small unsophisticated web site gets hacked the details get sold on the dark web and attackers use scripts to try the same password on the main email accounts until they find one that works.
Some phishing attacks don’t use email. A common method recently was automated calls or text messages, supposedly from Amazon, telling people their Amazon Prime membership was being renewed and stating the price, the message included a number to call if you didn’t want it renewed. On ringing through to this number, the victim gets a con artist who uses various techniques to gain the customers credit card details e.g. “Give me all your credit card details so I can process the refund”. Another method is callers pretending to be from Microsoft or BT to fix your IT issues – like that would ever happen.
How to spot a phishing scam
We’ve all seen simple and amateurish emails with bad grammar or poor English trying to get us to click on a link or opening an attachment, but some phishing attacks are getting very sophisticated. The things to look out for when trying to spot a phishing attack are:
If something is too good to be true then it probably isn’t. Emails saying you’ve won the lottery when you don’t even play it, winning competitions you didn’t enter, or offering to make you a fortunate helping a Nigerian prince launder his money are clearly only going to do one thing, lose you a lot of money.
Banks asking for personal information. Banks will never ask you for pin numbers and never get you to send account details in an email. If you think a bank email is suspect then call the bank using the number on the back of your bank card to check.
As mentioned above if the email has poor spelling, or poor grammar and phrasing then it’s likely a scam email.
Email using generic greetings like Dear Sir/Madam, or Dear Valued Customer are usually suspect. Genuine companies will use your real name.
Emails from complete strangers should be viewed with suspicion
Emails from high ranking people in your company, for example asking you to transfer money or pay a supplier, usually with an urgent deadline, should be questioned. Call the individual concerned to check they sent the request.
Emails from suppliers changing their bank details. A similar example of this sort of phishing attack was where an attacker got access to someone’s email account and, using the forward and move rule mentioned above, monitored messages and saw one from a builder with an invoice for repairs to a chimney. The attacker knocked up an identical invoice but with different bank details. The unsuspecting victim paid the invoice, why wouldn’t he as he was clearly expecting it, and lost a few thousand pounds.
Emails with “click here” links where the link clearly doesn’t look like a genuine address, or uses a similar clone or typo squatting address
Poor quality logos in emails that are just scrapped off the website
When you click on a link check for warnings from your browser. Also check the web site is https and has a padlock symbol in the address bar.
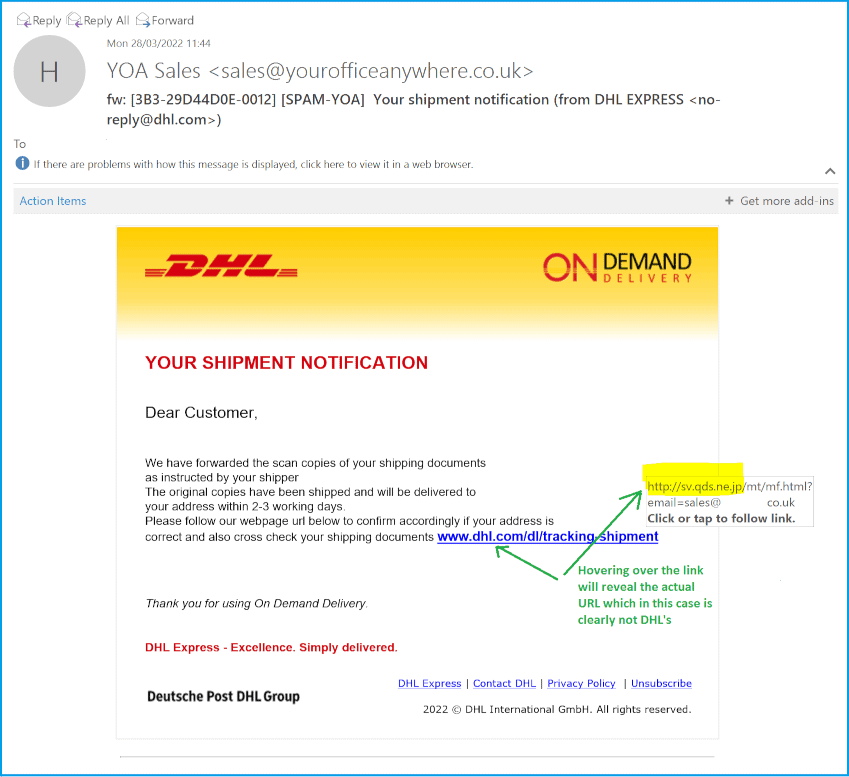
An example of a Phishing Email:
How to prevent employees falling victim to phishing scams, especially home workers
Don’t get me wrong, home workers are no more likely to fall for phishing attempts than anyone else, but the other safeguards that may be in place for office-based workers may not be available to home workers. Even the option of leaning over to a colleague and saying “does this look dodgy to you?” before clicking on a link or opening an attachment is not so easy for remote workers.
Putting measures in place to avoid phishing attacks is always going to be an arms race, hackers get more and more sophisticated and in the current world many attackers are state sponsored, working for their governments. However, there are some important steps businesses and individuals can take to reduce the risk of falling victim to phishing, and business managers should take a coordinated approach with multiple layers of protection:
Most importantly, training. Educate all staff to recognise phishing attacks.If someone knows what a phishing attack looks like they will be better prepared to avoid it. Many cyber security companies have systems to send pretend phishing emails so you can see which staff fall victim to it. Also educate employees on careless browsing.
Don’t blindly click on links in emails or open attachments. If there are links that you think you do need to click then hover your cursor over them to make sure they are genuine.
Make sure you have spam filters in place on your company email. Most of the big providers do this by default but there are still many smaller providers that don’t bother. If you host your own Exchange email for example then you should invest in spam filters as a matter of course.
Use security software on mobile devices, and VPN software on anything connecting through a public network.
Make sure computers have supported operating systems, and where possible the most up to date operating systems. I’ve seen cyber-attacks hitting a network and encrypting all the Windows 2012 servers (which are still supported) but not touching the 2016 or 2019 servers.
Always have automatic updates enabled on operating systems and latest versions of core software like Office, Adobe Reader, and browsers.
Always have antivirus software and other security software. Many antivirus software vendors have free versions, these are better than nothing but the paid for versions have multiple layers of protection and can more easily be managed to make sure no devices on your network fall through the cracks.
Don’t become complacent because you have antivirus software running. AV may stop you getting a virus, but won’t prevent you from entering your bank details into a fake website.
Use Multi-factor Authentication aka two-factor authentication on everything you can, especially your email account. Even if an attacker has your password he will be thwarted if you use multi-factor authentication.
Never email sensitive information such as usernames or passwords, unless they will be changed on first logon, in which case log on quickly and change them.
Double check senders email addresses, look for strange spelling, and unexpected variations. Service.amazon.co.uk is probably fine but amazon-service.co.uk could potentially be a completely spoof domain.
Don’t trust business emails coming from generic email address like Gmail or Yahoo.
Never interact with phishing emails or text messages that you know are fake. It may be tempting to email or text back and tell them what you think of them, but at the very least you’ll verify your address is real, and at worst you’ll end up on a “suckers list” and traded on the dark web.
Never use the same password twice, and always invest in a good password manager so you only have to remember one password. Never use your password manager password for anything else.
If you get a call from your bank or credit card company, hang up and call them back from a different phone using the number on your bank card.
If you get an email message from your bank or other finance firms like PayPal, don’t click it, instead go to your bank site the normal route and then look for messages, the message should be waiting for you, if not then it’s probably a scam.
How to mitigate against phishing and other cyber attacks
Let’s face it, someone in your organisation, possibly you, will inevitable click on the dodgy link or get infected my malware via another route. So, look for ways of reducing the impact on your business if the worst happens.
Most importantly, back up your data, then back it up again to somewhere else, off site. It’s always good policy to have 3 copies of your data, one of which should be in an “air gapped” offsite location. If the very worse happens and your entire IT network gets ransomware then full backups are your only way to get back up and running. Equally as important, know how to recover your systems from backups, practice this at least quarterly.
Reduce privileges, if an attacker or malware gets access to an employee’s computer they can only cause problems to the data and systems that the employee has access to. Work on the basis of least privilege. Reduce access to sensitive information or personal data to only those that really need it.
Think about your company culture, would your staff be confident enough to challenge an urgent email from the MD asking them to transfer money or pay a supplier.
Make sure staff understand the regular and usual business arrangements and to question things if they are not sure. Do they know how your bank would usually communicate with you, do they know when to expect invoices from suppliers and in what format?
Put checks in place for common scams such as suppliers changing their bank accounts.
Report and share all suspected attacks. Share a screen shot of obvious phishing emails so colleagues know how to spot them.
Never punish staff who fall victim to phishing attacks, this will discourage reporting and you may lose the opportunity to fix things such as running full antivirus scans.
Check your digital footprint, are you giving away too much information to scammers on your company website and social media presence. Be wary about how much information suppliers and contractors put on their website about your company. Does that Case Study give away a little bit too much information about your company structure?
Help staff understand about the potential impact of sharing company and personal information on social media.
Consider how your own outgoing emails look and whether they could be misinterpreted as phishing emails.
Keep up to date on phishing trends, check the National Cyber Security Centre website.
What to do if you know you’ve fallen for a phishing scam
You’ll hopefully know it as soon as it happens. Maybe you entered your bank account details into a fake website and realise it isn’t the real thing when you can’t see your balance, or your computer is infected by a virus, maybe crypto lockered. What are the first steps you should take to minimise the impact?
Some quick things you can do if you realise early enough are things like unplugging your computer from the network or turning off Wi-Fi. This will reduce the chances of a virus spreading to your colleague’s computers or company server.
Use a different computer, ideally one on a different network, to change your email password. Email is used by most sites to change passwords so accessing your email account will give hackers access to everything else.
Check your email rules to make sure no one has set a forwarding rule.
Run a full antivirus scan on your computer.
Contact your bank or other sites for which your details may have been stolen. Contact credit card company and ask them to freeze or change your card
Report the scam to the authorities. Contact Action Fraud and Citizens Advice. Register with the Credit Industry Fraud Avoidance System (CIFAS) if you think your identity has been stolen. You can report suspected phishing emails to report@phishing.gov.uk which is run by the National Cyber Security Centre (NCSC)
End all communication with the scammer immediately
Update other passwords where you think you may have been compromised. If you have broken the golden rule of using the same password for other sites then change that password on every site that may use it.
Your Office Anywhere are one of the country’s longest established providers of hosted remote desktop services which are a great way of helping people to work from home. For more information on hosted desktops please contact us on 01282 500318 or complete the contact form below.
Contact us here for a fast response
Call Us
+44 (0)1282 500318
Office
Your Office Anywhere, 4 Dominion Court, Billington Road, Burnley, BB11 5UB
Hours (Sales)
M-F: 9am - 5pm
S-S: Closed